Are you protecting yourself against ransomware in the cloud-first era?
Over the last couple of years, as businesses have done more and more to accommodate remote and hybrid work, they’ve been moving to the cloud in...
3 min read
![]() Zones
:
Oct 2, 2018 7:11:02 AM
Zones
:
Oct 2, 2018 7:11:02 AM

A generation ago, good data protection strategies were all about tape backup. In smaller companies, someone simply took the tapes home; in larger companies, offsite vaulting filled the bill. If the place burned down, you were covered. Back then, stealing data meant figuring out how to create and spirit away bulky reels of magnetic tape without being seen. Needless to say, that wasn’t a big issue for most companies.
But with the rise of WANs, LANs, the internet, and the cloud, security became far more challenging because all that connectivity created a target-rich environment for hackers.
In response, sales of firewalls, encryption, and an array of endpoint and network protection tools grew to become an industry of their own.
But even the best traditional security measures can’t protect against human nature and human error. Intentionally or inadvertently, our coworkers can easily direct company data to places it should not go.
Whether it’s a well-crafted phishing attack that tricks a team member into giving a bad actor access to the network or a well-meaning developer improperly sharing source code with a colleague via a cloud storage app like Dropbox, your workforce can open the organization up to significant data security risks. Likewise, shadow IT – those unauthorized but legitimate cloud applications that workers use – brings a whole new category of potential threats to corporate data.
“Once data moves to the cloud, the ability to control your data is really tested,” says Todd Leeson, Partner & Product Management vice president at Zones, “but DLP and CASB can help mitigate the risks”.
Leeson is referring to Data Loss Prevention (DLP) solutions paired with Cloud Access Security Brokers (CASBs), a combination that can monitor traffic for specific categories or strings of data as they move across on-prem devices and networks, as well as off-site colocation centers, cloud apps, cloud platforms, and cloud storage services.
“Comprehensive DLP solutions use a combination of advanced technologies to detect and protect confidential data in motion and at rest and can also enforce policies around compliance and privacy issues like HIPAA, GDPR, and PCI DSS,” explained Leeson. “By incorporating a CASB, IT can extend that protection and those policies to the cloud as well.”
The advantage of using a CASB for the enforcement of cloud DLP is that CASBs are 100% focused on securing cloud services. CASBs maintain a registry of cloud services with detailed and up-to-date signatures for each application. These signatures enable the CASB to understand the traffic to and from a cloud service and enforce DLP policies.
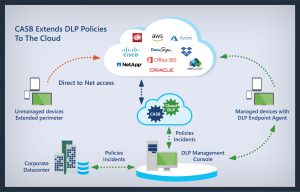 CASBs integrate with on-premises DLP solutions via ICAP, a standard protocol for sending content to a DLP solution for inspection. To integrate with an on-premises DLP solution, the CASB uses a piece of software on premises that serves as a connector. The CASB can enforce DLP policies against existing data in a cloud service and new files as they are uploaded. When a CASB is connected to a cloud service via API, the CASB’s cloud platform scans it for document metadata and passes a list of documents to the CASB’s on-premises connector requiring deeper inspection.
CASBs integrate with on-premises DLP solutions via ICAP, a standard protocol for sending content to a DLP solution for inspection. To integrate with an on-premises DLP solution, the CASB uses a piece of software on premises that serves as a connector. The CASB can enforce DLP policies against existing data in a cloud service and new files as they are uploaded. When a CASB is connected to a cloud service via API, the CASB’s cloud platform scans it for document metadata and passes a list of documents to the CASB’s on-premises connector requiring deeper inspection.
The connector downloads files directly and passes them to the DLP solution for content inspection. The DLP solution inspects files against its existing DLP policies. When the DLP solutions identifies a violation, it sends the violation to the CASB cloud platform via the connector. The CASB cloud platform enforces remediation action with the cloud service via API. For example, a CASB can take a quarantine action for a file containing sensitive data, quarantining the file in place in the cloud service so the end user can no longer access it. Once the file is quarantined, the CASB cloud platform notifies the on-premises DLP solution via the connector so that remediation action is registered in the solution for closed-loop reporting.
While it’s a DLP or CASB solution’s job to track the flow of information, they can’t define the characteristics of the data you want to monitor. Data classification provides the permanent and explicit identification labels that DLP systems need to correctly process the data.
“It’s fairly easy to set up the policies in a DLP or CASB,” said Leeson. “But as your implement, the most important thing is to build in time for proper data classification and time for trial – to make sure your policies are clear, precise, and tuned to eliminate the false positives.”
For effective data loss prevention, a DLP or CASB solution must be taught what to flag and what action to take when data is flagged. That can range from encrypting the data, to denying the ability to copy, to preventing access entirely. Without precise data classification in place, data governance will be imprecise as well.
“The security professionals at Zones are a great resource for companies that are implementing a DLP solution or extending their DLP framework to the cloud with a CASB,” said Leeson. “Prior to implementation, they’ll consult with a business’ IT security team and structure or conduct a data classification project that will speed time to value.”
Speaking of value, comprehensive DLP and CASB solutions are not going to break the bank – particularly when you consider the potential cost of a breach or theft in terms of competitive advantage, fines, or legal fees. Committing $50,000-$100,000 to a robust security solution today could help avoid ten times that expense in the future.
 This article originally appeared in the Fall 2018 edition of Solutions by Zones magazine.
This article originally appeared in the Fall 2018 edition of Solutions by Zones magazine.

Over the last couple of years, as businesses have done more and more to accommodate remote and hybrid work, they’ve been moving to the cloud in...

In today's digital age, IT security is essential for any business. As our reliance on technology and the internet rises, the risk of cyber-attacks...

While there’s no such thing as an easy year in a complex, dynamic field like technology, 2020 has been particularly challenging for corporate IT...